Cyber Security
Your organization’s sensitive data needs to be heavily protected and encrypted. But can your teams securely access, share, and analyze your confidential data?
Oves’s Data Clean Rooms enable secure collaboration and analytics on confidential data powered by our Confidential Computing technology.
























NIS DIRECTIVE COMPLIANCE SERVICES.
LEGAL REQUIREMENTS
- Directive (EU) 2016/1148 The Directive on security of network and information systems (the NIS Directive) was adopted by the European Parliament on 6 July 2016 and entered into force in August 2016. Member States have to transpose the Directive into their national laws by 9 May 2018 and identify operators of essential services (OES) by 9 November 2018.
- National Law - NIS Directive transposition
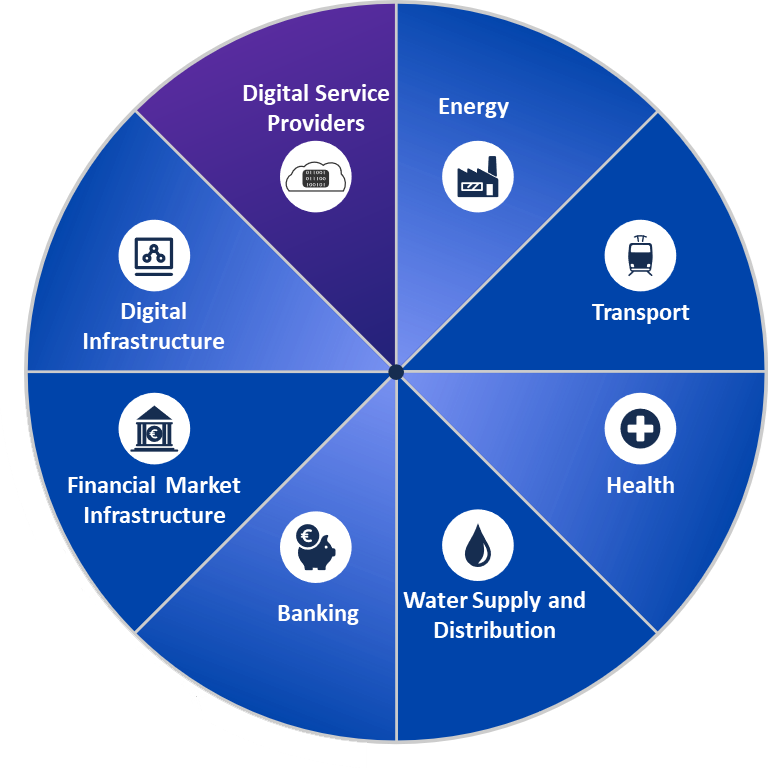
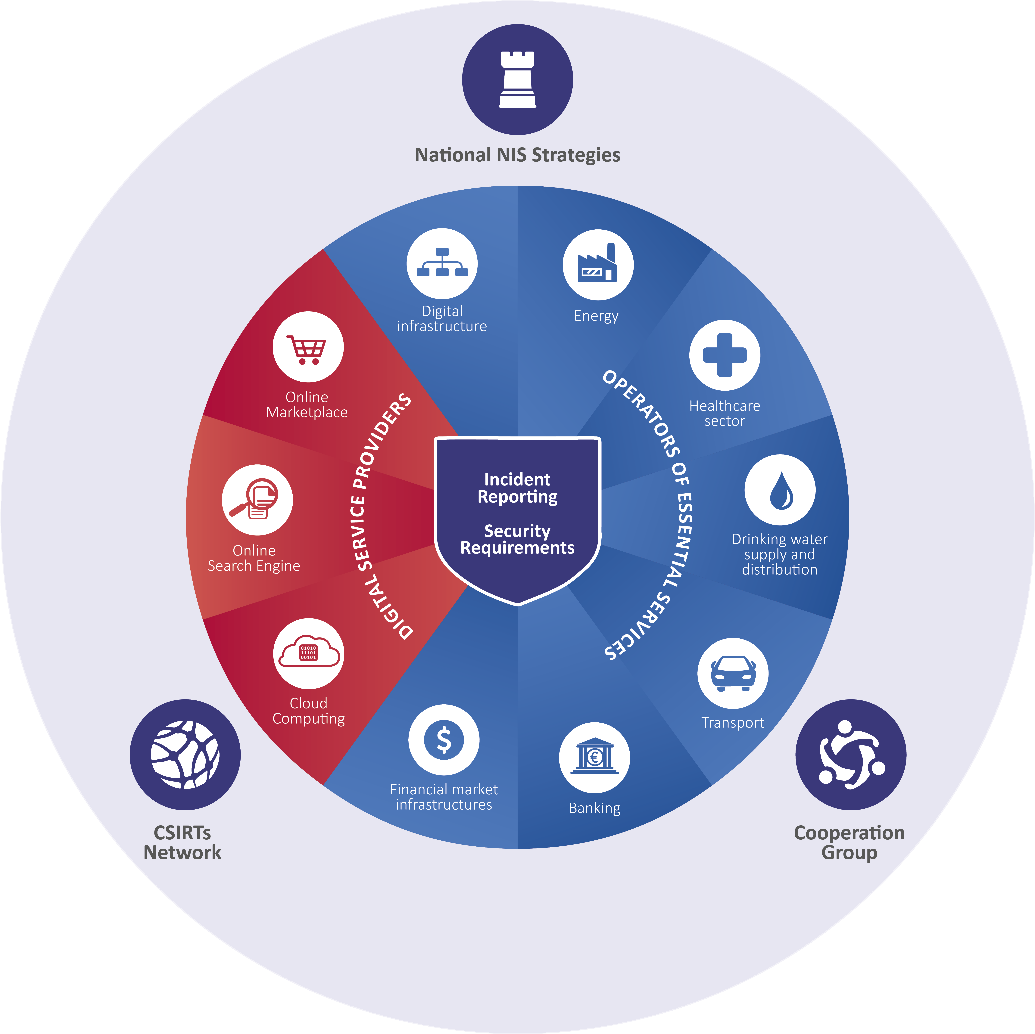
OSE – ESSENTIAL SERVICES OPERATORS
- Organizations in the following industries:
- Energy - electricity / oil & gas
- Banking and financial market infrastructures
- Public and private healthcare
- Transport - road / air / rail
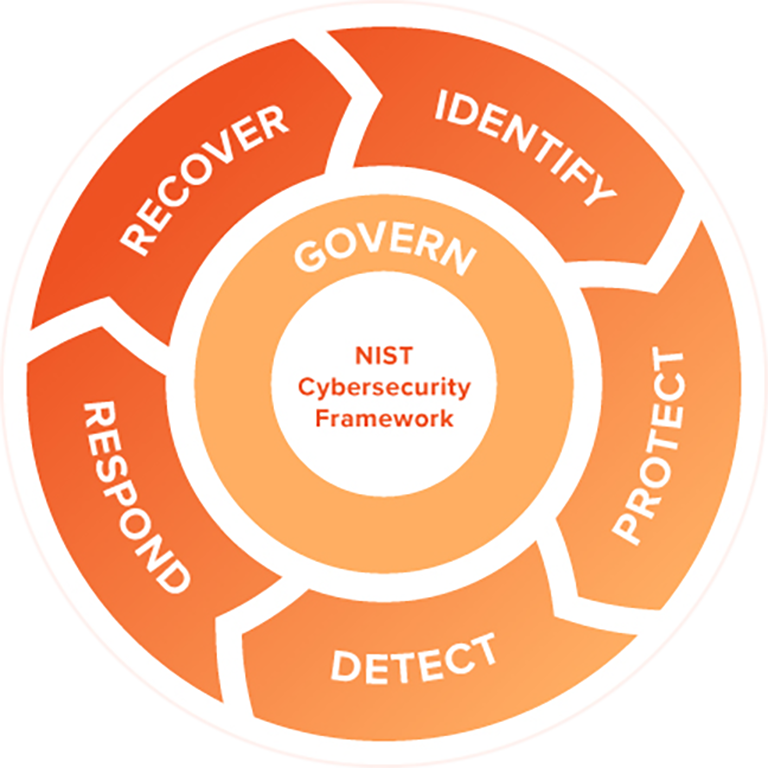
GAP Analysis based on Cyber Assurance Framework
Risk Management
- Governance
- Risk management
- Asset management
- Supply chain
Security event detection
- Security monitoring
- Proactive discovery of security events
Protection against cyber attacks
- Protection policies and procedures
- Identity and access control
- Data security
- Systems security
- Resilient networks and systems
- Training and awareness
Minimize impact of incidents
- Incident response and recovery planning Improvement
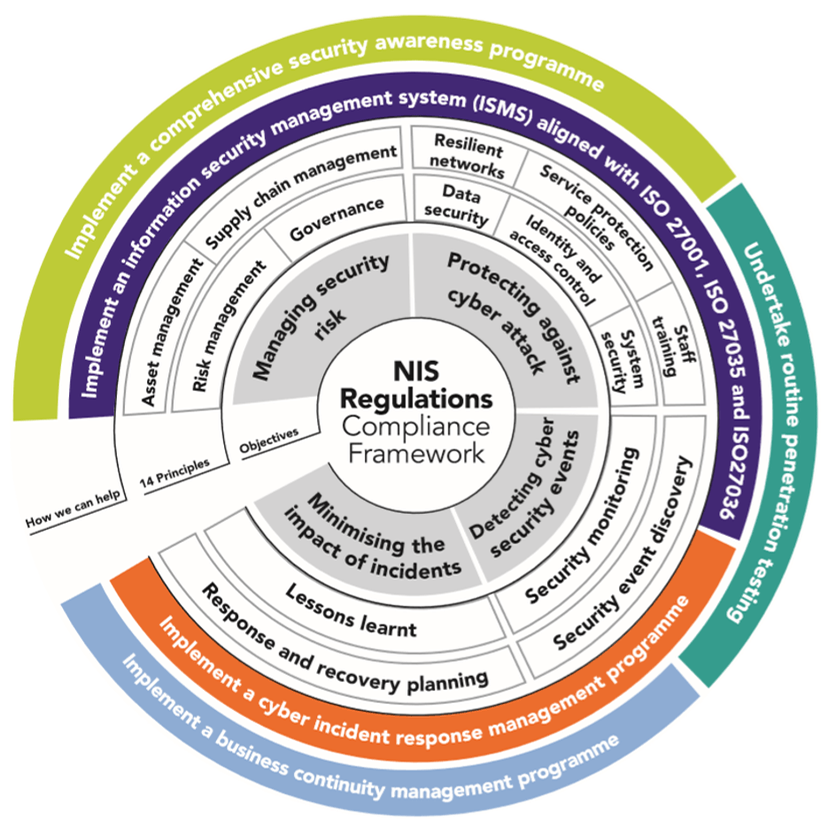
NIS REGULATIONS COMPLIANCE FRAMEWORK
Essential Services Operators shall take appropriate measures to:
- Manage risks to security of networks and information systems
- Prevent and minimize impact of incidents affecting the security of networks and information systems to protect continuity of services
- Notify, as soon as possible, the competent CSIRT of incidents that may have a significant impact on the continuity of provided essential services
COMPLIANCE SUPPORT SERVICES
Gap Analysis
- Identify gaps and corrective actions
- Plan / prioritize / estimate
Build organisational capabilities:
- Risk management framework
- Policies and procedures
- Incident response and recovery
- Supply chain security
- Training and awareness
- Competence assessment
Security assessment
- Security audit
- Penetration testing
Design and implement technical controls
- Event monitoring / discovery / analysis
- Data security
- Asset management
- Identity & access management
- Security operation center
Certifications
Read more ...Development of Information Security Program
Read more ...Risk Management / Audit / Assurance
Read more ...Identity and Access Management
Read more ...Penetration testing
Read more ...CISO as a Service
Read more ...Microsoft Security
Read more ...Fraud Prevention
Read more ...